Konnech's Shocking "Back-Door" Access Into U.S. Election Data: Network Diagram
Los Angeles County prosecutors allege "Chinese contractors" had "superadministration" access to “astounding” amounts of data in what is "probably the largest data breach in United States history.”
Oct 18 2022
Eugene Yu, the CEO of Michigan-based election software company Konnech, was criminally charged for allegedly storing Los Angeles election worker data on Chinese servers.
Los Angeles County prosecutor Eric Neff alleges that the amount of data involved in the breach was “astounding,” adding that “this is probably the largest data breach in United States history.”
The prosecutor’s complaint reads:
“Based on evidence recovered from a search warrant executed October 4, 2022, the District Attorney’s Office discovered that Konnech employees known and unknown sent personal identifying information of Los Angeles County election workers to third-party software developers who assisted with creating and fixing Konnech's internal ‘PollChief’ software.”
The complaint claims that Luis Nabergoi, a Konnech project manager overseeing the Los Angeles contract, wrote in a Chinese-owned messaging app that "any employee for Chinese contractors working on PollChief software had 'superadministration' privileges for all PollChief clients."
Sam Faddis, retired CIA operations officer and renowned national security author, wrote in his Substack:
“An individual with super administration access to a system can do effectively anything inside that system. He or she can delete data, steal data, alter data, change programming, etc.
Perhaps most importantly, that individual can cover his or her tracks, because they can potentially also access and alter all security protocols and programs.
So, Konnech, which has numerous questionable ties to Chinese entities was allowed to punch a hole into our election systems, and then Konnech was allowed to grant that same level of access to unknown “contractors” in China.”
I began investigating Konnech on August 13, 2022, after Catherine Engelbrecht of TrueTheVote and Gregg Phillips of OPSEC shared the story of their 15-month involvement with what was characterized to them as a “counter-intelligence operation” with the Federal Bureau of Investigation into Konnech that had gone bad.
When the Bureau turned against Engelbrecht and Phillips, the pair sought out researchers with whom they could share what they knew.
Weeks later a federal court judge granted Konnech a restraining order against Engelbrecht and Phillips, forcing them into an unprecedented legal battle.
Their silencing makes it all the more important that we continue to speak out about the now substantiated subversion of America’s elections.
While the Los Angeles District Attorney’s office acknowledges that Konnech uses “Chinese contractors” and “third-party software developers,” the prosecutors fail to name Konnech’s Chinese subsidiary.
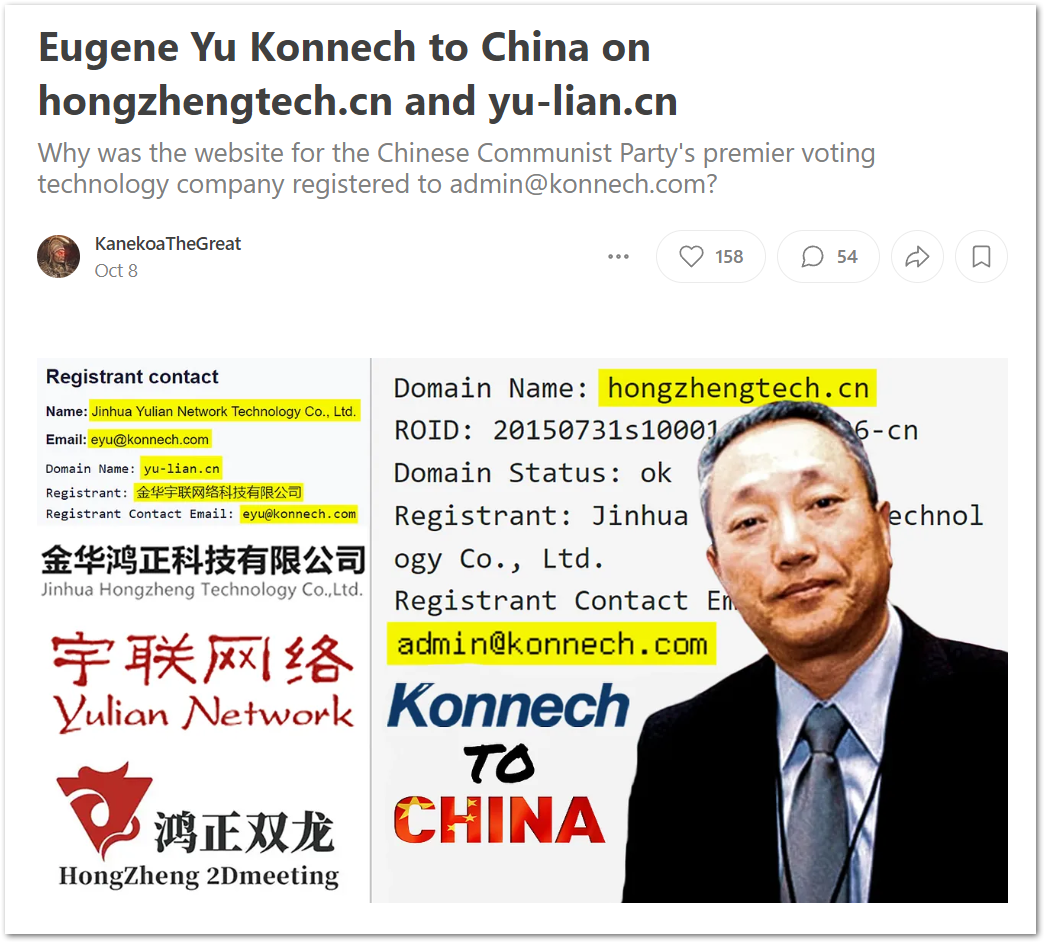
As I detail in my last two months of reporting and with recent confirmation from the New York Times, Konnech’s Chinese subsidiary is named Jinhua Yulian Network Technology (金华宇联网络科技有限公司).
Eugene Yu, also known as Jianwei Yu (于建伟), established his Chinese subsidiary in Zhejiang, China, on Nov. 29, 2005.
Yu, who graduated from Zhejiang University in 1982 and lived in China until 1986, registered his Chinese subsidiary's website "yu-lian.cn” to eyu@konnech.com on Feb. 25, 2006.
On a 2013 archived version of Yu’s website, the American election software CEO praised the vision of the former Chinese President, who he called “Comrade Jiang Zemin,” as he wrote in Chinese about his success with “Election Management Solutions Detroit” and “U.S. Overseas Voters.”
Chinese search engines reveal that as recently as 2018, Konnech’s Chinese subsidiary bid on Chinese government contracts to provide “electronic voting systems” to China’s National People’s Congress.
Patent transfers, employee profiles, and domain registrations divulge that Konnech is also profoundly connected to another Chinese election software firm named Jinhua Hongzheng Technology (金华鸿正科技有限公司).
Hongzheng Technology operates in more than 20 provinces across China in partnership with Lenovo, Huawei, China Telecom, China Unicom, and China Mobile as the premier voting technology provider for China’s National People’s Congress.
The Federal Communications Commission (FCC) has designated China Telecom, China Unicom, China Mobile, and Huawei as “national security threats.”
Eugene Yu registered Hongzheng Technology’s website “hongzhengtech.cn” to admin@konnech.com on July 31, 2015.
Yulian Network’s and Hongzheng Technology’s track record of developing election software for the Chinese government puts Konnech into an incredibly compromised position.
One can easily imagine a scenario in which Chinese government-linked election software companies embed malicious spyware into software products to be re-branded by an American subsidiary and sold in the United States.
Contrary to popular belief, malware is abundant, and infections can be very stealthy and hard to spot, enabling hackers to dwell on networks for months or years silently.
In 2020, a Chinese bank instructed a multinational technology company doing business in China to install software to pay local taxes.
A cyber security firm said the tax software was legitimate, but embedded inside it was a “sophisticated piece of malware that gave attackers complete access to the company's network,” NBC News reported.
In 2021, Massachusetts-based cyber security firm Recorded Future discovered spyware in an app named “Beijing One Pass” that foreign companies operating in China are forced to install.
The In-Q-Tel-funded cyber security organization said that the app was “developed by a Chinese state-owned company” and included hidden features such as the ability to; record screenshots, capture keystrokes, and disable security.
In other words, it is not beyond the capabilities of “Chinese contractors” linked to China’s National People’s Congress to deeply embed malicious spyware into seemingly harmless software that silently infiltrates, monitors, captures, and sends stolen data back to its developers.
On Aug. 10, 2021, Los Angeles County’s election office uploaded a network diagram of its Election Management System (EMS) called “EMS Future State v15” to the county registrar’s website.
A network diagram is a digital roadmap that identifies data flow within an organization.
Los Angeles county’s diagram demonstrates that Konnech’s PollChief software has a direct “data integration” and “data exchange” point with the county’s overall EMS software.
According to the county’s diagram, PollChief appears to integrate with all kinds of voter information; "Voter Registration," "Voter Records," "Election Night Reporting," "Address Verification," and "Ballot Layout," among other data moves to that same “data integration” and “data exchange” point.
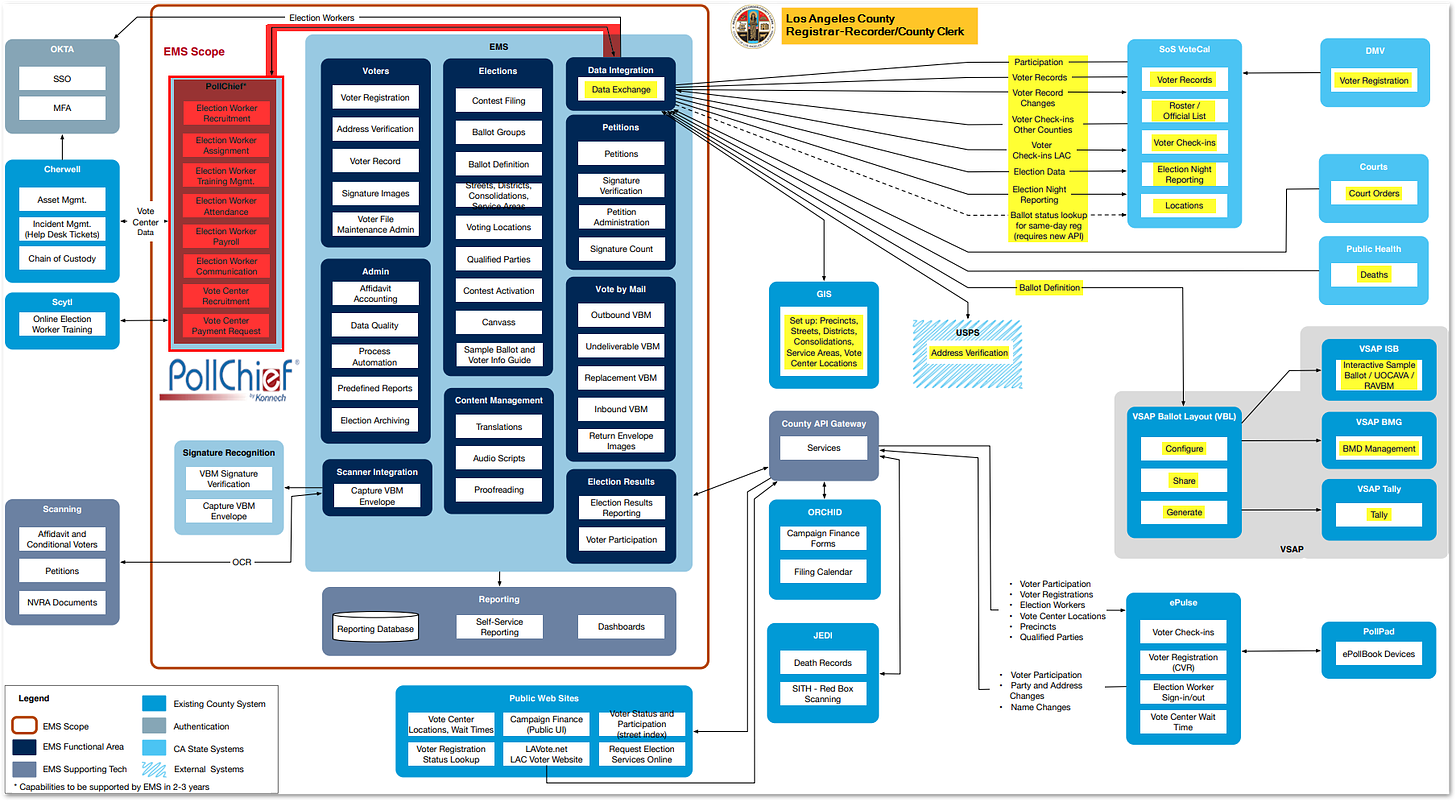

The team at electionfraud20.org, a collective of software developers, data scientists, and engineers who study election system vulnerabilities, say that Los Angeles county’s network diagram shows that “You are giving massive back-door access to all the critical election subsystems that are required to rig the election, in a way that no one will ever notice. And you are giving it to Chinese developers.”
“If PollChief is compromised, this diagram shows that the whole election management system is compromised.”
Common sense dictates that “Chinese contractors” linked to China’s National People’s Congress should not be developing U.S. election software.
Suppose those same “Chinese contractors” had “superadministration” access to U.S. election data since Eugene Yu first launched his Chinese subsidiary in Nov. 2005.
In that case, one can easily imagine why Los Angeles prosecutors allege that “astounding” amounts of data were breached in what is “probably the largest data breach in United States history.”


No comments:
Post a Comment
Comments always welcome!