Hackers Sneak Malware Into Apple App Store 'To Steal iCloud Passwords'
It’s been a busy week for the Apple AAPL +0.92% iPhone security team. First there was a serious flaw in iOS that could have allowed malware to sneak onto devices via the AirDrop filesharing service. Later in the week, it emerged scores of Chinese apps hosted on the official Apple App Store were infected with some dodgy code siphoning off information from users’ phones.
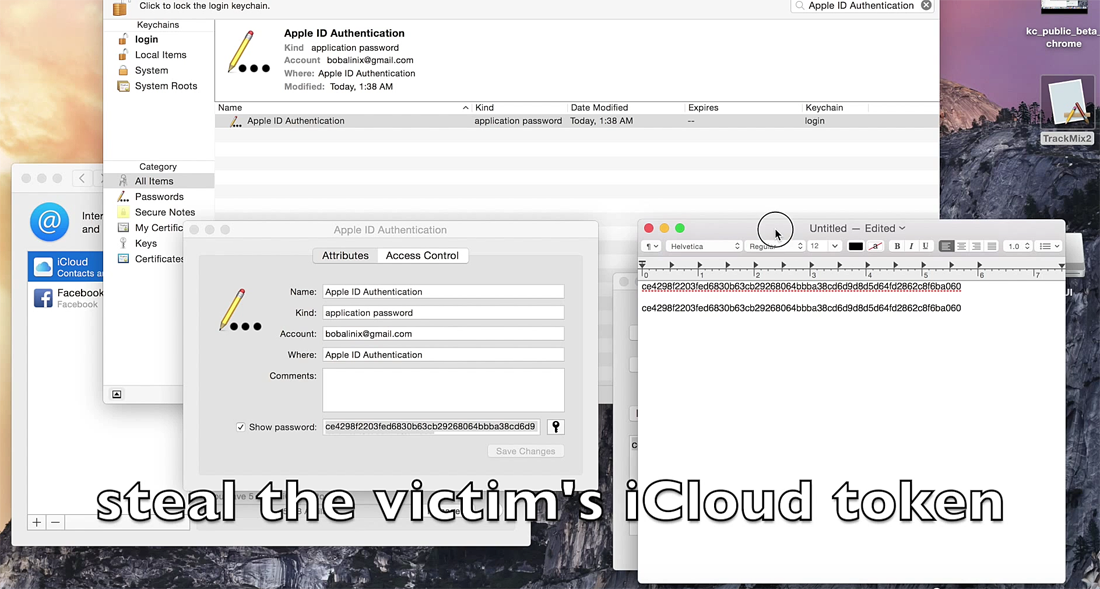
The App Store malware breakout is worse than first thought, however, with security experts claiming today that WeChat, a hugely popular messaging and social networking app, and Didi Kuaidi, Uber’s chief rival in China, carried the threat. The attackers, FORBES understands, are hunting for iCloud login details amongst other data.
The route to infection was somewhat convoluted but sensible from the perspective of the perpetrators. They sought to abuse trust in third-party downloads of Xcode, the developer tool for iOS and Mac OS X apps. Many developers had chosen to grab Xcode from theBaidu cloud file sharing service rather than straight from Apple. But somehow those downloads had been tweaked to add malware to apps constructed with the altered Xcode, so they would grab seemingly innocuous data from iPhones, such as device name and basic network information. Researchers from Chinese tech titan Alibabaaptly dubbed the rogue code XcodeGhost.

Palo Alto Networks discovered malicious code was served from Baidu’s cloud and made its way into Apple’s App Store.
The malware is not so subtle, however. Palo Alto Networks senior malware researcher Claud Xiao told FORBES the firm had discovered that though it first appeared apparently non-sensitive data was taken by the malware, “it can be remotely controlled by the attacker to phish or exploit local system or app vulnerabilities”. That makes XcodeGhost potentially more dangerous and it seems to be an entry point onto iPhones for further exploitation.
Ryan Olson, intelligence director of the Unit 42 research unit at Palo Alto Networks, explained further: “After contacting the command and control server to upload information about the infected device, the malware retrieves an encrypted response from the server. This response contains multiple possible commands. One of them specifies a message to send to the user in the form of an alert prompt.
“We have evidence that this was used to ‘phish’ iCloud credentials from users of infected apps. The response can also contain a URL which the app will then open. We don’t know how this is being used, but it could be used to send other apps on the phone to potentially malicious resources.”
It initially seemed the infections were contained to Chinese apps and largely affected Chinese users. But today it became apparent a far larger range of apps were infected, affecting hundreds of millions of users across the world, according to US-based Palo Alto Networks. The firm noted that CamCard, the most popular business card reader and scanner in the US and many other countries, contained XcodeGhost.
Netherlands security intelligence provider Fox -IT, meanwhile, performed its own analysis of the traffic containing stolen data and found a slew of other apps were affected, many of which were not connected to China. The full list of infected apps can be found onPalo Alto Networks’ blog.
Tencent has updated the WeChat app to get rid of the bad code, noting in an online statement that it had found no evidence of data loss. According to its post, Palo Alto Networks is working with Apple to address the issue. Baidu has also removed the evil files from its cloud. Apple had not responded to a request for comment at the time of publication.
Whatever the eventual impact on users, malware has found a way around Apple’s strict App Store protections. It’s been proven beforeand it’ll be proven again: even the most locked-down environments can be breached.
No comments:
Post a Comment
Comments always welcome!